Feature-Based Method in Text Steganography: Evaluating Single-Bit and Dual-Bit Techniques for Secure Hidden Message
Keywords:
Text steganography, feature-based technique, single-bit technique, dual-bit technique, embedding capacity size bitAbstract
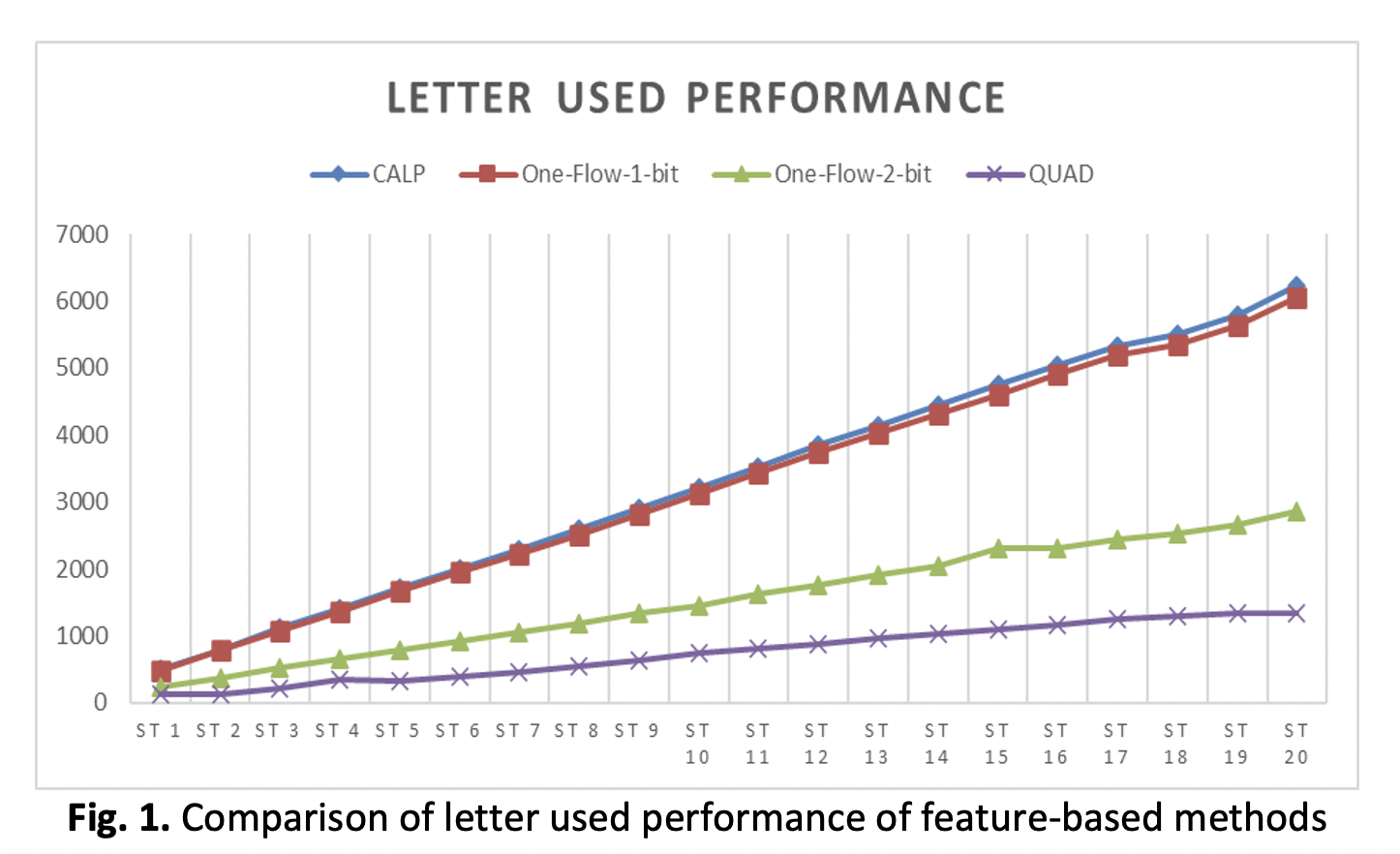
Steganography, the art of concealing information within other non-secret data, has gained prominence as a method for secure communication. Among its various forms, text steganography particularly feature-based techniques offers a discreet approach by embedding messages within the structural characteristics of text. However, challenges persist in balancing data capacity, security, and imperceptibility. This paper aims to analyze and compare four feature-based text steganography techniques: two single-bit methods Change Alphabet Letter Pattern (CALP) and One-Flow-1-bit and two dual-bit methods One-Flow-2-bit and QUAD. Each technique utilizes distinct visual and structural features of English letters. This paper employs a comparative methodology, evaluating the techniques based on letter usage efficiency and embedding capacity. Results indicate that while single-bit methods like CALP offer simplicity and precise embedding for short texts, they are limited in capacity. In contrast, dual-bit techniques, particularly QUAD, demonstrate superior data embedding capabilities, making the technique suitable for scenarios requiring higher security and larger data concealment. However, increased complexity in dual-bit methods may impact processing efficiency. The study concludes that selecting an appropriate technique depends on the specific requirements of the application, such as the volume of data to be hidden and the desired level of covertness.